This week, another major secure email gateway provider aka anti virus provider, announced new features to deal with the growing problem of business email compromise (BEC) or email spoofing. Business Email Compromise (BEC), CEO email abuse, spear phishing, whaling, email domain spoofing – these are some of the terms that are used to describe a specific attack against an organisation where a key aspect in the attack is the use of their email domain.
The attack typically involves the use of the email domain somewhere in the email header to impersonate a legitimate email from that organisation. This process works best in conjunction with the weakest link in the chain, namely the Human ! Our brains relate well to the familiar so when we see an email that looks like it came from someone we know, we immediately stop thinking and click the link or the attachment and BANG we just opened the door to a malicious virus or ransomware and the rest of our working week will becoming very stressful !!
We discussed how the weakest link has now moved to the executive level in a previous blog – Executives-CxO-level-targeted-in-CEO-email-abuse-scams. It is a perception by most that our senior executives are not as computer literate as they should be. This generalisation is not entirely accurate, but leaders such as Senator Hillary Clinton having issues with understanding email only perpetuates this perception.
There are some simple techniques that you can do – that you should do in my humble opinion – before you rush out and purchase or upgrade to the next latest and greatest appliance or secure email gateway. Beyond being a keen believer in the KISS principal, these simple techniques below can be considered “best practice” in relation to securing your email domains. In many ways, focusing on the email gateway first before these simple techniques are completed is like putting the cart before the horse, it typically works better the other way – Porsche or VW are the exception.
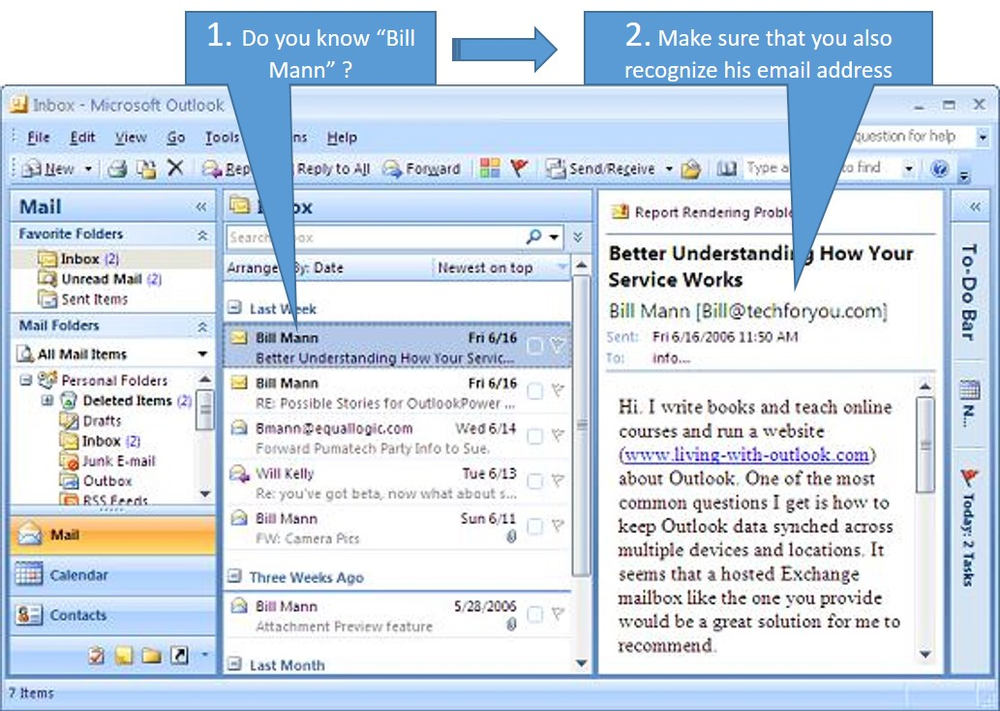
1.“Preview Pane” must be opened Train your users to operate their email, whether it is the typical Microsoft Outlook or a web browser based Gmail or Yahoo account, with the “preview pane” opened. This simple technique not only identifies the user but also the actual email sender. Please see the diagram below. If you don’t recognise the email address, please have IT investigate. Additionally, it may indicate that it was sent by a 3rd party email sender, such that it will show “Bill Mann [ Bill@bulkemail.com on behalf of Bill@techforyou.com] – alert IT again if it seems suspicious. Please also consider a broader security training awareness program for groups of staff or all employees.
2. Implement SPF, DKIM and DMARC SPF, DKIM and DMARC can be considered part of the initial steps when deploying an email platform, and definitely when upgrading to a newer version. There is no point having a fancy alarm system ie secure email gateway, when the doors and the windows of the house are kept wide open. SPF and DMARC are authentication mechanisms that are maintained in the domain’s public DNS that provide strong confidence to the recipient that the sender is who it says it is. DKIM provides another layer of authentication in that it confirms the payload ie email body or contents are authentic and tested with a public key received by the recipient with a private key held by the sender. Check this blog for further details – Starting your SPF journey ? Add DMARC for greater success ! 3. Layered Security Standardisation is a great concept but when it comes to security, I would advocate that a layered approach is best. With all things being equal, all anti virus providers release updates at different intervals based on their detection techniques. Certainly the on-premise email gateway should be a different vendor to the cloud web and email gateway vendor. And please don’t forget about the internal endpoint and server protection. With points 1 and 2 completed, you can now focus on the purchase of the anti virus or secure email gateway. Of course these steps are not meant to be in sequential order, but what’s important is to have them implemented.
Stay Alert. “An ounce of prevention is worth a pound of cure.” — Benjamin Franklin
By Con Lokos
