Sharing information is an important method to raise awareness of any potential issue. With the addition of practical advice, the reader can identify the relevance of that information and its usefulness to mitigate an issue.
Reading this article again and again I keep on focussing on aspects that haven’t been addressed – of course there’s only so much space that articles can utilise.
So herein lies some practical information that I believe is important to several stakeholders, namely:
Consumer – the reader of the article and specifically those in the UK that obviously would receive HMRC emails – FYI this organisation is the country’s tax department.HMRC themselves – this is the PRIMARY brand under attack by cyber criminals, andUniversity of Oklahoma – this is the SECONDARY brand under attack – why so ? See below it will become clearer.
For convenience, I have attached the image of the phishing email that the article sourced from Malwarebytes.
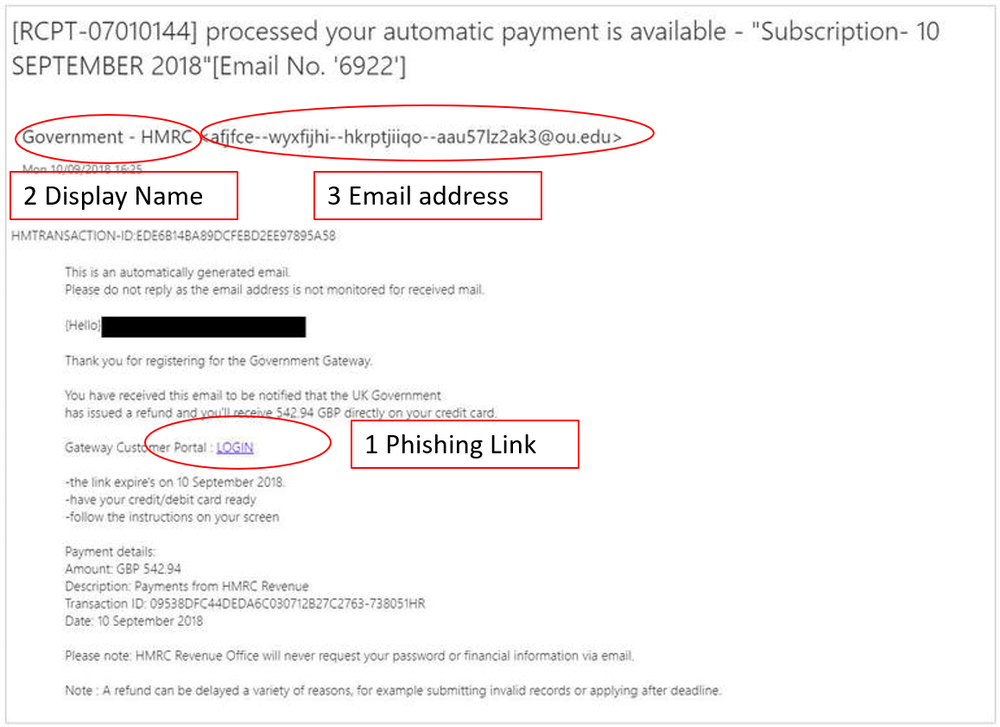
As part of any analysis conducted by any Security Operations Centre, I would hope that they look at more than just the phishing link – item 1 in the above image.
Equally important is item 2 – “display name” and also item 3 – “Email address” – both also known as the RFC5322.FROM address.
The display name is what we see when we use Outlook email client or similar.
The display name is just text and is unfortunately not policed or validated as part of the email standard. This is what we see in our email client such as Outlook. This element is an important piece of the overall email that formulates our perception that the email is real of fake. We covered a simple technique to overcome this issue in the aptly named “Simple Techniques to mitigate Business Email Compromise” available here. By previewing or opening the email, we can see the original email address – item 3.
The email address in item 3 is also a text field and unlike item 2 “display name”, this field can be policed and validated thanks to the DMARC standard (RFC 7489). Additionally, many email inbound processing gateways, Cisco, Barracuda, Fireeye, Symantec, etc may also perform a reputation check on this field. This is the reason why cyber criminals use a valid domain name in the field to leverage the reputation of well known email domain with the hope of sailing through the email verification checks.
Let’s take it back to that image and what other actions can be taken:
- Consumers should appreciate that the email address they see in their email client could be fake. For instance from the image we can safely say that it is fake as HMRC would never send an email from ou.edu.
Government – HMRC
Spend the little extra time to open the email and see the email address.
- HMRC – the primary brand should educate its customers either via their website or through social media about how email is sent to them and what email domains they use. For example, HMRC may only send emails from the following domains – noreply@hmrc.gov.uk or noreply@info.hmrc.gov.uk for example. Undergo a DMARC Compliance project and move those legit domains/subdomains to a reject policy. Popularise the message regularly via social media of all valid domains and subdomains. Make the weakest link a strong link !!
- Secondary brand- University of Oklahoma (OU.edu) – It would be useful that the primary brand, HMRC, communicated with the secondary brand that is used in the phishing campaign firstly as way of professional courtesy to inform them that their primary email domain is being used illegitimately in a phishing campaign. Yours truly has advised OU of the phishing campaign and I hope they take credence to my advice. Secondly, this information would be useful for both brands in potentially creating countermeasures to mitigate the phishing campaign. Finally, it would be highly recommended that OU also undertake a DMARC Compliance project and move to reject asap.
I’m sure that I have armed most readers of this article with some useful and simple insights. I’m sure now we will do the right thing and pay it forward with your friends and colleagues.
by Con Lokos
